WiFi Deauthentication Frames Explained
Deauthentication, or, in short, “deauth” frames are an infamous part of the WiFi protocol (802.11) and play a role in many types of attacks on wireless infrastructure. They have the important and legitimate use-case of actively disconnecting stations from networks, but can also be easily abused because they are almost always unencrypted and easily spoofed or crafted.
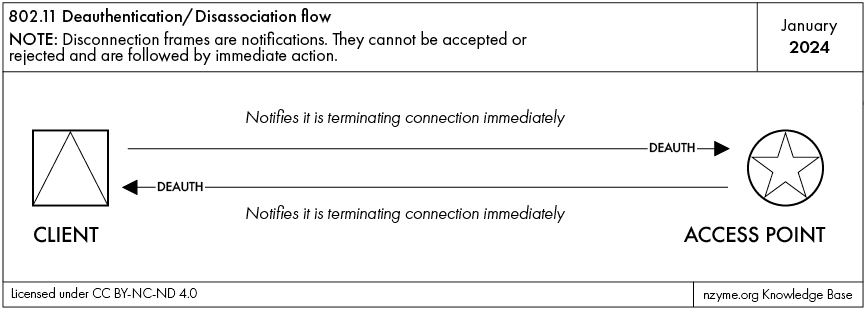
It is important to know that deauthentication frames are instructions and not requests. The receiving station cannot refuse a deauthentication or disassociation.
Two Frame Types: Deauthentication / Disassociation
Even though you will often hear about deauthentication frames, there is another and very similar frame type: The disassociation frame.
While a deauth frame instructs to entirely disconnect from a wireless network, a disassoc frame instructs to only
disassociate from a specific access point while staying authenticated with the network. The result, however, is that
the client will no longer be able to use the network until it re-authenticates or re-associates.
A typical situation for a disassociation frame could be an access point going into scheduled maintenance mode and instructing all connected clients to connect to another access point in range before it shuts down. The authentication remains valid in this case.
A deauthentication frame is used when a client is disconnected (or disconnecting) from the entire network and not just a specific access point. The client cannot re-connect without re-authenticating again.
We will mostly refer to deauthentication frames in this article.
Frame Structure
The relevant parts of a deauthentication frame are in its MAC header and frame body.
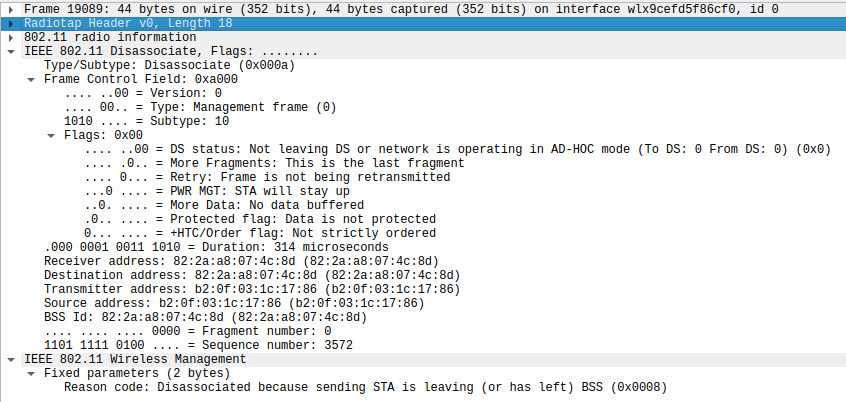
The MAC header contains the destination and transmitter addresses, indicating which station sent the frame and what station it is addressed to.
The frame body can additionally contain “vendor-specific” information, but must contain a reason code. The reason code defines for what reason the frame was sent, providing context about the action that was taken. Remember: Deauthentication and disassociation frames are instructions and not requests. The receiving side cannot accept or deny the activity and must act accordingly.
Legitimate Uses
Deauthentication frames are an important part of WiFi networks and help maintain orderly connection management and user experience.
Some legitimate uses of deauthentication frames include:
- A time-limited connection to a network is no longer valid and an access point cleanly disconnects the now expired client by sending a deauthentication frame. This way, the client will not have to wait for a timeout to realize it has been disconnected and can provide a much better user experience.
- A access point reboots and disassociates all its connected clients so they can connect to another access point seamlessly.
- A client is turning off WiFi and disconnecting. The client sends a deauthentication frame and allows the access point to immediately clear allocated resources like entries in the association tables.
There are dozens of different possible “reason codes” for deauthentication frames defined in the 802.11 WiFi standard.
Deauthentication “deauth” Attacks
Maliciously crafted and spoofed deauthentication frames are part of two broad types of attacks:
- Use for jamming: Continuously deauthenticating all clients in range will effectively prevent any WiFi connections to be established. Hardware cost for this can be as low as $10 and hardware for it is readily available.
- As part of a larger WiFi attack campaign: Targeted deauthentication of clients can be used to force the station to connect to another access point that is under control of the attacker. A social engineering angle in this pattern includes the use of deauthentication frames to annoy a human so much that they start to manually look for other available networks - and those could be under attacker control.
You can find a more detailed dive into this topic in the Deauthentication Attacks Explained knowledge base article.
Analyzing Deauthentication Activity in Wireshark
You can see all recorded deauthentication frames using the following Wireshark filter:
wlan.fc.type == 0 && (wlan.fc.type_subtype == 10 || wlan.fc.type_subtype == 12)
This selects all management frames (wlan.fc.type == 0) and the deauthentication as well as the disassociation
frame types (wlan.fc.type_subtype == 10 || wlan.fc.type_subtype == 12.)
Analyzing Deauthentication Activity in nzyme
Nzyme collects all deauthentication and disassociation frames and summarizes the activity on the “Disconnection” page.
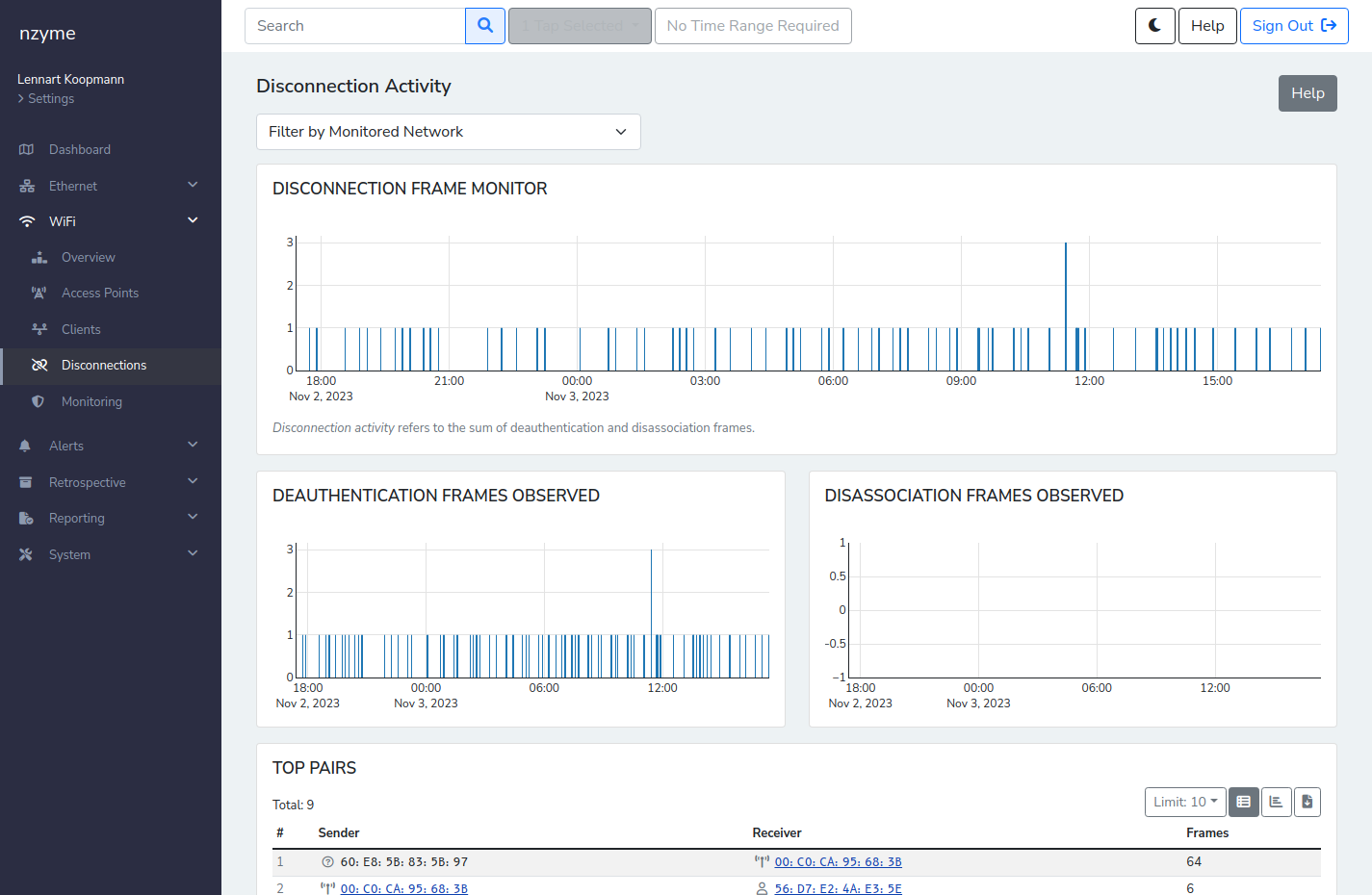
You can learn more about analyzing disconnection activity in the nzyme documentation.