Nzyme v2.0.0-alpha.9 has been released
Happy New Year if your calendar is of the Gregorian kind! We are back from some relaxing holiday weeks and have been at work since. Today, we are releasing nzyme v2.0.0-alpha.9. We did skip alpha.7 and alpha.8 due to bugs discovered immediately after version tagging.
Let’s look at what’s new!
Changelog
- New Feature: WiFi Monitored Network Configuration Import
- New Feature: WiFi Restricted SSID Substring and Similar SSID Alerts
- New Feature: WiFi Protected Management Frames (PMF) Detection
- New Feature: WiFi Client and Access Point signal strength by tap
- Improvements to WPA3 detection and handling of different WiFi security suites
- Reliable handling of NULL bytes and empty characters in SSIDs
- Fingerprint debugging
- Many bugfixes and improvements. Some are fairly large. Please let us know if anything stopped working or was better before.
New Feature: WiFi Monitored Network Configuration Import
You have to add every access point serving your network, together with their fingerprints, security settings and used channels to your configuration if you want to fully monitor it. This is not very hard to do if you have one or two access points at home, but becomes a real problem if you have hundreds of access points, possibly operating on several different WiFi bands.
We added the long awaited configuration import feature in this release.
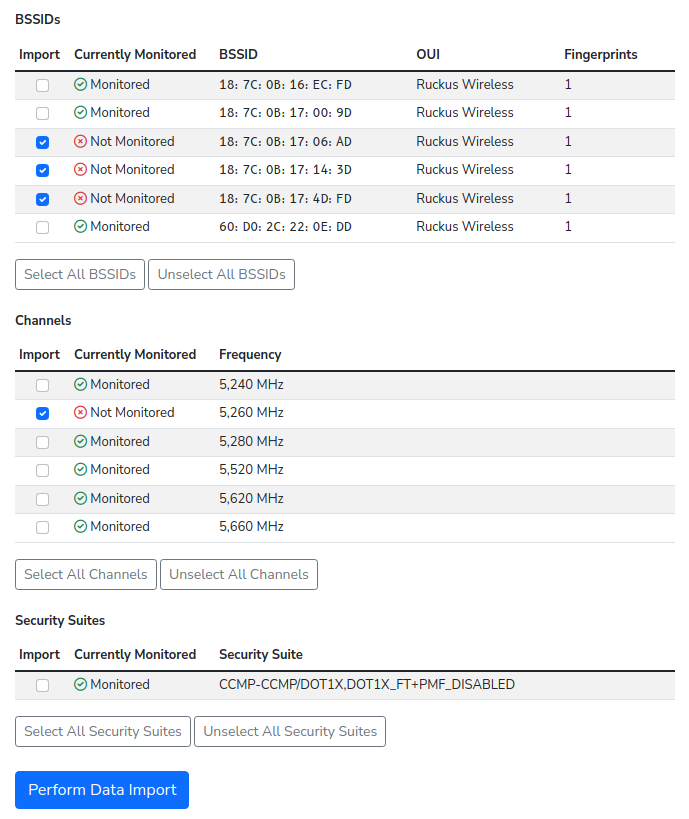
You can now use the configuration that nzyme already collects about your network and automatically add it to the monitoring configuration.
Of course, you should always cross-check the imported configuration with a known-good state to prevent the accidental import of BSSIDs and other data associated with potential bad actors already active within your network environment.
This will save a lot of typing and copying and pasting.
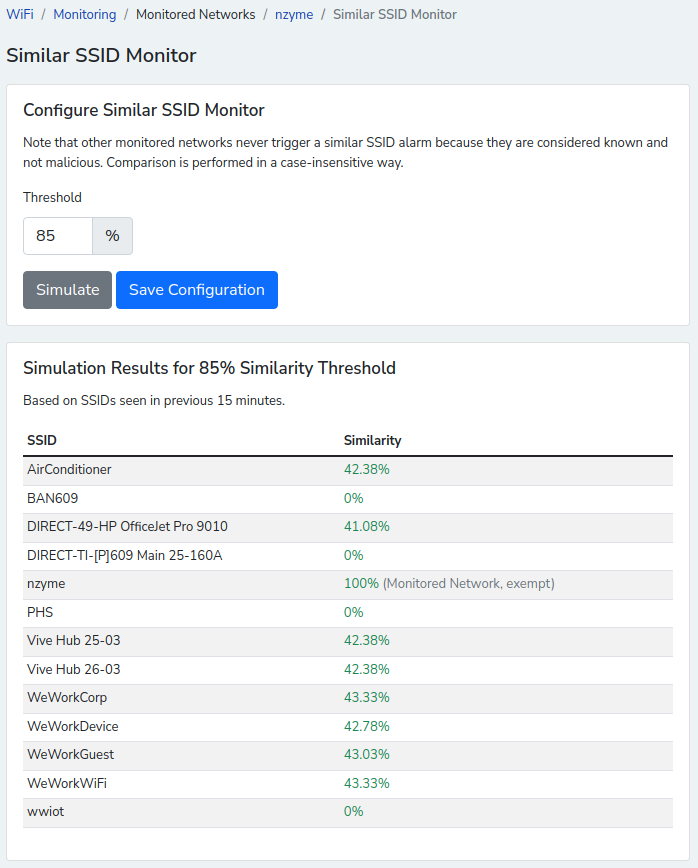
New Feature: WiFi Restricted SSID Substring and Similar SSID Alerts
An attacker could try to lure you or your colleagues to join a network under their control using a similar sounding SSID.
For example, let’s say your legitimate network is called UmbrellaCorp and a new network called UmbrellaCorpGuest or UmbrelaCorp (with one l) under the control of the attackers appears. Would you find this out in time before someone connects to it? Even worse, an attacker may use a deauthentication attack to knock devices off the network and make people look for legitimate sounding alternatives.
Two new alerts in nzyme cover this:
- You could set up the Restricted Substring alert for the substring Umbrella and receive an alert the moment a network with a name including that string appears.
- You could set up the Similar SSID alert and be alerted because the UmbrelaCorp (with one l) crosses your configured similarity percentage threshold.
New Feature: WiFi Protected Management Frames (PMF) Detection
WiFi networks can enable Protected Management Frames (PMF) when using WPA2 or WPA3. PMF protects some types of management frames from being spoofed or recorded in cleartext by listeners. They must be required in WPA3-secured networks and can be disabled, optional or required in WPA2-secured networks.
Adoption is increasing but not very widespread yet because of compatibility issues in many WiFi devices.
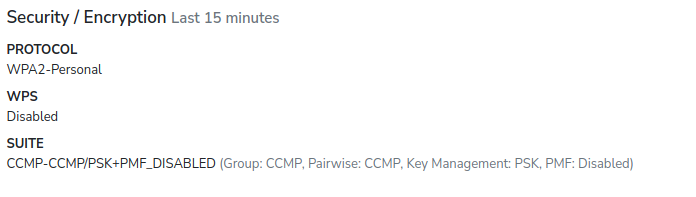
Starting with this release, nzyme is recording the PMF setting for each SSID and adding it to the security suites string.
For example, the nzyme security suites string of a WPA2 network with disabled PMF now looks like this:
CCMP-CCMP/PSK+PMF_DISABLED
You have to adapt existing monitored security suite strings because of this added parameter. This is covered in the upgrade notes.
New Feature: WiFi Client and Access Point Signal Strength by Tap
The BSSID and client details pages are now showing the recent average signal strength per tap:
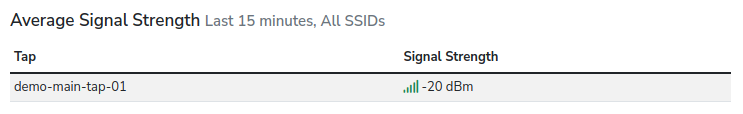
This is a small change but part of a larger addition of signal strength analysis and … dare we say it … physical location mapping.
We are also starting to collect client signal strengths with this release. You can expect a waterfall histogram analysis like for access points in the next release.
Improvements to WPA3 Detection and Handling of Different WiFi Security Suites
We improved the part of the tap code that decides what security protocol (None/Open, Enhanced Open, WEP, WPA1, WPA2, WPA3, WPA3 192 bit, various transition modes) a SSID uses. This change introduces added accuracy and fixes some bugs in the old code. We are now reliably detecting the security protocol and show more information.
On top of that, we improved how we collect and display networks that are advertised with different security settings during a single tap collection cycle. We are now accurately detecting if, for example, the same network is advertised as an open network and a WPA2 network - a common situation when rogue access points are in action.
Reliable Handling of NULL Bytes and Empty Characters in SSIDS
SSIDs support unicode. This does not only mean that you can add emojis to your network names (you are welcome), but also that crafty attackers can use confusing unicode characters to trick someone to connect to their malicious WiFi.
For example, an attacker could include NULL bytes or “empty characters” in the SSID - invisible to the human eye and not rendered on your phone or laptop network list.
This new nzyme release is filtering out NULL bytes and empty characters from SSIDs. This way, nzyme is seeing the network names like a human eye would and can effectively alert on any malicious attempts related to SSID crafting. The above-mentioned similar sounding SSID and restricted SSID substring alerts will just transparently work, no matter how clever an attacker gets with invisible characters. The same applies to all other network monitoring alerts that will now pick up on it.
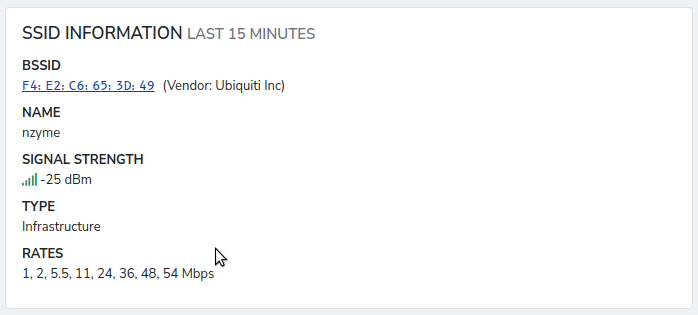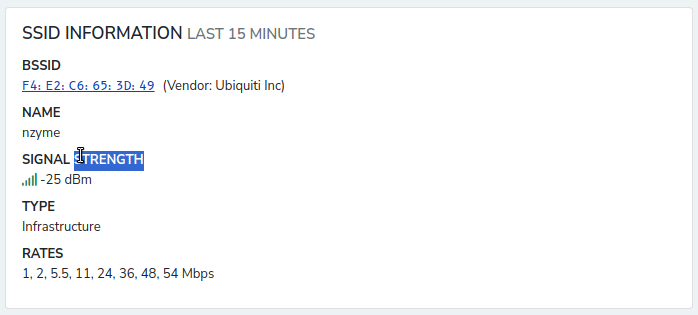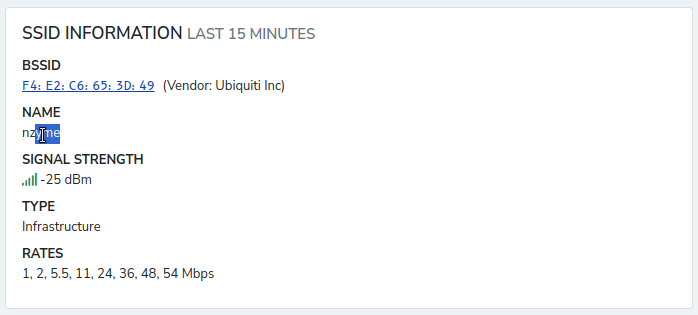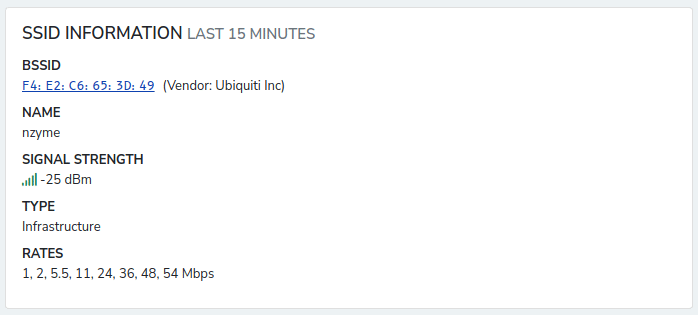
Fingerprint Debugging
Sometimes nzyme may record more than one or two fingerprints for a transmitter, rendering the fingerprint-based detection methods virtually unusable. You can now enable fingerprint debugging to find out which frame parameters are causing the changes in fingerprints.
This new feature is documented here.
Download & Upgrading
All packages are available for download on the downloads page. Upgrading is easy. Please follow the release notes on the downloads page.
New installations should follow the installation documentation.
How can I help?
You are some of the first users to try out nzyme v2.0.0, and we are looking for any kind of feedback:
- What didn’t work, what bugs did you experience?
- What was confusing or seemingly unnecessarily complex?
- What is missing?
- What do you think should be changed?
Again, this is an early release and no feelings will be hurt.
You can file issues on GitHub, join the nzyme Discord or post in the discussion forums to provide your feedback or ask questions.